Protect Your Data & Patient Privacy
/Global technological threats are growing. Privacy is breached knowing that anyone can access your information from your smartphone or computer, without even having grab hold of it. The WannaCry hack is a wake-up call for everybody, which should prompt everyone to raise their security levels.
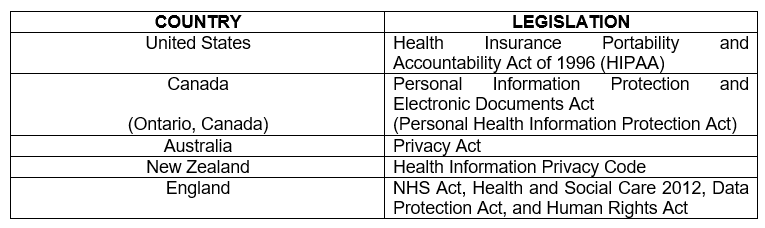
 It is important that physicians should be able to protect their patient’s privacy. Cosmetic and aesthetic physicians should take caution most especially considering the nature of their treatments and procedures.
It is important that physicians should be able to protect their patient’s privacy. Cosmetic and aesthetic physicians should take caution most especially considering the nature of their treatments and procedures.
Imagine the the following scenario; you get an email one morning that all of your patient before and after photos have been stole and if you don't pay $20k in Bitcoins by noon, they'll be posted online.
What do you do? Are you going to pay or wait until noon and see if all of your patient's before photos are posted and...